Create Your Own AI Girlfriend 😈
Chat with AI Luvr's today or make your own! Receive images, audio messages, and much more! 🔥
4.5 stars

Yes, you absolutely can verify a user's age without forcing them to upload a government ID.Verifying someone's age without demanding a government ID is not just possible—it's often a smarter approach. Solutions like credit card checks, mobile carrier data, or biometric age estimation are leading the way. These modern methods strike a crucial balance between legal compliance and user privacy, creating a much smoother experience than the old-school ID upload.
Why Traditional ID Checks Are Failing Online Platforms

The classic "upload your driver's license" model is hitting its expiration date. Let's be honest, in a world where data breaches are practically a weekly news headline, people are more skeptical than ever about sharing sensitive documents online. This is especially true for platforms with adult-oriented content, where privacy isn't just a preference—it's a requirement.
That initial friction point during sign-up? It’s a huge reason why potential users just give up and leave.
This isn't just about privacy paranoia, either. It’s a real-world accessibility problem. A massive chunk of the global population, especially younger adults and people in developing regions, simply don't have a government-issued photo ID. The World Bank estimates that around 850 million people worldwide lack official identification. Relying on ID verification automatically locks out this enormous audience.
The Problem with High-Friction Verification
For any platform that needs to ensure users are adults, this creates a major roadblock to growth. When you demand an ID, you risk alienating a huge part of your target market and eroding trust from the very first click. Today's users expect a seamless and secure process that doesn't feel like an interrogation.
The core challenge for modern platforms is not just about blocking minors but doing so in a way that doesn't punish legitimate adult users with invasive and cumbersome verification steps.
Instead of building a relationship, rigid ID checks do the opposite. They send a clear message that you might not care about user privacy. For services in the adult entertainment or online dating world, that can be an absolute deal-breaker. Users need to feel safe and anonymous, and a mandatory ID upload is a direct threat to that feeling. This is why knowing how to verify age without an ID is so critical for both compliance and keeping your users around.
Shifting Legal and User Expectations
Thankfully, regulations are starting to catch up with reality. The conversation is moving away from just collecting proof of age to responsibly assuring it in a privacy-first way. This shift is being pushed by a few key trends:
- Growing Privacy Concerns: People are savvier than ever about their digital footprint and are demanding more control over their personal data.
- Technological Advancement: We now have new tools that can reliably estimate age without ever needing to see or store a physical ID document.
- Regulatory Flexibility: Forward-thinking laws, like the UK's Online Safety Act, are promoting a risk-based approach. This allows for different levels of assurance depending on the type of content being accessed.
Platforms that don't adapt are going to get left behind. It's not just about losing users; it's about failing to meet modern standards. After all, if you have an underage policy, you have to enforce it effectively, and relying solely on an outdated method like ID checks is no longer a viable or user-friendly strategy.
The Pitfalls of Common Age Verification Methods
Before we dive into a better way of handling age verification, we need to talk about why so many common methods just don't cut it. Honestly, these traditional approaches often create more headaches than they solve, leaving you with frustrated users and a flimsy legal defense.
Let's break down why these popular methods fall short.
The most basic, and frankly, laziest method out there is the simple self-declaration checkbox: "I confirm I am over 18." It’s frictionless, sure, but it offers zero real protection. Anyone can click "yes" without a second thought, which makes it completely useless for genuine age assurance. From a compliance standpoint, this method is a non-starter and gives platforms a dangerous false sense of security.
Despite its obvious flaws, self-declaration is still everywhere. A huge reason for this is that younger people simply don't have government-issued IDs. Think about it: just over 1% of 14- and 15-year-olds and only 43% of older minors even have one. You can dig into more of this data and see why so many platforms default to self-attestation on the AVPA website.
Why Facial Age Estimation Isn't a Silver Bullet
So, what about something more advanced, like facial age estimation? The idea sounds great—a user snaps a quick selfie, and an AI tells you if they’re old enough. While it's certainly a step up from a checkbox, this technology is riddled with accuracy problems, especially around critical age thresholds like 18.
An algorithm might guess a 17-year-old is 19, or worse, flag a legitimate 20-year-old as underage. These aren't just minor glitches; they can lock out your actual target audience and create a terrible first impression of your platform.
The core problem with many facial estimation tools is their inconsistency. Performance can swing wildly depending on demographics, lighting, and even the quality of a user's phone camera, leading to biased and unreliable results.
Worse still, studies have shown that these systems can be less accurate for certain ethnic groups and women. This introduces a serious element of bias that can tarnish your brand's reputation. If you value inclusivity and fairness, relying solely on a technology with known demographic weaknesses is a massive risk.
To really see the difference, it helps to compare these methods side-by-side.
A Quick Look at Common Age Verification Methods
This table breaks down the most common age verification methods, giving you a clear picture of their effectiveness, user friction, privacy implications, and overall reliability.
| Method | Accuracy | User Friction | Privacy Risk | Best For |
|---|---|---|---|---|
| Self-Declaration | Extremely Low | None | Low | Low-risk content where compliance is not a major concern. |
| Facial Estimation | Moderate-High | Low | Moderate | Quick, low-friction checks for platforms that can tolerate a margin of error. |
| Credit Card Check | High | Low | Moderate | E-commerce or paid services where users already have a card on file. |
| Third-Party Provider | Very High | Low-Moderate | Low (with trusted partners) | Platforms needing robust, compliant verification without handling raw PII. |
As you can see, the simpler methods come with major trade-offs in accuracy and reliability. Understanding where these common approaches fail is the first step toward building a better system. It really drives home why a multi-layered, privacy-first strategy is the only way to go if you're serious about verifying age without demanding an ID.
Practical ID-Less Verification Methods You Can Use Today
Let's be honest, asking for a driver's license online is a surefire way to kill your conversion rates. It’s clunky, intrusive, and users hate it. The good news is, we've moved far beyond those outdated methods.
You can build a robust, compliant age verification system without ever needing to see a government ID. These are real-world, practical strategies that protect your platform and create a smooth journey for your legitimate users. The trick is to be smart and layer your approach, making the whole process nearly invisible to the adults you want to welcome.
Tap Into Financial and Telecom Data
One of the most reliable (and low-friction) signals of adulthood is access to financial services. It's a simple fact of life: you generally have to be 18 or older to get your own credit card or open a bank account. This makes financial data an incredibly powerful proxy for age.
Credit Card Checks (AVS): This is a classic. By processing a tiny, refundable charge (even just $1.00), the Address Verification System (AVS) instantly matches the user’s billing info with what the card issuer has on file. Since adults are the overwhelming majority of credit card holders, a successful AVS check is a very strong indicator of age.
Bank Account Verification: With user consent, modern open banking APIs can confirm a user's age directly with their bank. Your platform asks the question, and the bank simply sends back a "yes" or "no" response. No sensitive financial data is ever shared, making it both private and effective.
Mobile phone contracts work on a similar principle. Most are signed by adults, so telecom data can add another layer of confidence. Some carriers, for instance, already apply age filters to new SIM cards that block adult content until the account holder proves they're over 18. You're essentially tapping into a verification check that's already been done.
Use Third-Party Identity Networks
Why reinvent the wheel? Building and maintaining a compliant verification system from scratch is a massive undertaking. Instead, you can plug directly into secure, established identity networks that have already done the heavy lifting.
These specialized services have verified the age of millions of users across the web. When a new user signs up on your site, you can ping the network, which checks if that person already has a verified age attribute.
The real beauty of this approach is its simplicity. The network gives you a straightforward "yes, user is over 18" or "no, user is under 18" answer. This radically minimizes your data liability and protects user privacy by sharing only the absolute minimum required.
This method not only makes your onboarding flow faster but also ensures you're backed by experts who live and breathe compliance and privacy law. As you're tightening up your user flows, it’s also a good idea to secure other potential weak points. For example, our guide on how to securely verify an email address provides some complementary security insights.
The Power of Layered Verification
Here’s where it all comes together. No single method is foolproof, which is why the most resilient systems layer multiple checks into a smart verification funnel. You start with the easiest, lowest-friction methods first and only escalate to more demanding checks when a user fails or the initial signal is weak.
Think of it like a series of gates. A user might first pass a quick check using their mobile carrier data. If that gives you a high-confidence result, fantastic—they’re in. If the signal is inconclusive, your system can automatically trigger the next step, like a credit card check.
The diagram below maps out what a typical escalation path looks like when initial checks don't pass.
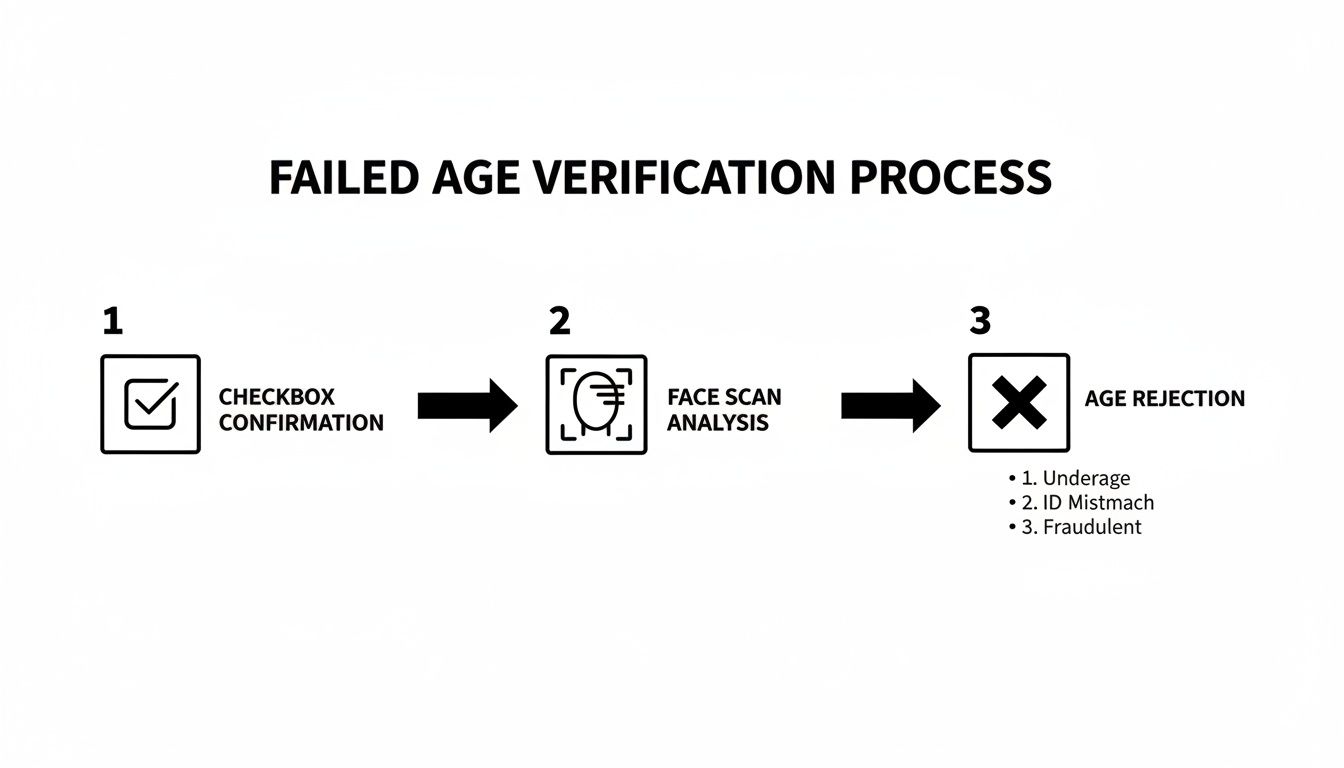
As you can see, the user journey can flow from a simple checkbox to a more advanced face scan if needed, leading to a definitive "no" if they can't meet the age requirement. It’s all about building a flexible, intelligent system.
The Future of Age Assurance is Privacy-First

Let's be honest, the way we think about age verification is changing. It’s no longer just a box-ticking exercise to meet legal standards. Today, it’s about earning and keeping your users' trust, which is everything on platforms built around sensitive or adult interactions.
The future isn't about collecting more data; it's about collecting less. The most innovative methods prove a user's age without ever compromising their anonymity. This new wave of tech is built on a simple but powerful idea: provide "age assurance," not a full-blown identity check.
Reusable Digital Tokens are a Game Changer
One of the most exciting developments I've seen is the rise of reusable digital tokens. The concept is refreshingly straightforward. A user verifies their age once with a trusted third party and, in return, gets a secure, anonymous digital token.
Think of this token as a digital passport for age-gated sites. It confirms they meet the age requirement without ever revealing who they are.
This is a win-win. Users are spared the tedious process of re-verifying on every new platform, and you, as the platform owner, drastically reduce your data liability. These alternative methods, especially device-bound attestations and tokens, are quickly becoming the gold standard for privacy-focused companies. The Electronic Frontier Foundation (EFF) has some great insights on this shift.
How Cryptographic Proofs Work Their Magic
Diving a bit deeper, we have cryptographic proofs, which promise to make age verification almost invisible to the user. These are often called zero-knowledge proofs (ZKPs), and they're as cool as they sound. A user's device can mathematically prove to your website that they are, for example, over 18, without ever sharing their actual date of birth.
It's like a bouncer at a club who instantly knows you're old enough without ever seeing your ID. Your system just gets a "yes" or "no," and all the user's personal data stays securely on their device.
This technology directly tackles the biggest privacy fears that stop people from engaging with age-gated content. When you adopt a method like this, you're sending a clear signal: you respect your audience and are serious about protecting their data.
For any platform, especially one like ours, nothing is more important than safeguarding user information. We believe in being upfront about how we handle data, a commitment we detail in our own Privacy Policy. The end goal is always to create an environment where users feel completely safe.
Ultimately, verifying age without an ID is about being smarter, not more intrusive. It's about using technology that respects user privacy by default, proving that security and a fantastic user experience can absolutely go hand-in-hand.
Building a Resilient System for Edge Cases and Fraud
Automated systems are incredibly efficient, but let's be realistic: no single age verification method is foolproof. It’s not a matter of if, but when a legitimate adult gets incorrectly flagged or a determined minor tries to game the system. This is precisely why a resilient, multi-layered approach isn't just a nice-to-have; it's your most critical asset for turning a potential roadblock into a smooth resolution.
The objective isn’t just about putting up a wall. It’s about creating a fair and transparent process for everyone involved. When your first line of defense—say, an automated check—returns a "fail" or is inconclusive, you absolutely need a clear escalation path. Without one, you risk locking out the very people you’re trying to serve.
Creating Fair Escalation Paths
Picture this: a 22-year-old with a baby face gets flagged by your facial age estimation tool. A hard "no" at this point is a recipe for a lost user. Instead, your system should instantly and gracefully offer them another way to prove their age.
This is where you pivot to fallback options:
- A quick credit card check: A small, immediately refundable authorization is a powerful secondary signal of adulthood.
- A light-touch manual review: If other automated methods fail, giving the user an option for a human to briefly review their case can solve tricky situations in minutes.
This kind of flexibility shows users you’re not just an algorithm; you’re a reasonable platform invested in getting it right. It’s a huge step in building trust, especially when you're dealing with technologies known for their quirks.
For instance, facial age estimation has become a popular method, but it struggles with accuracy right at the margins that matter most—like the line between 17 and 18. Research continues to show that these systems perform inconsistently across different demographics and can be off by several years, creating real potential for bias. You can read more about these technology findings and see exactly why having a fallback plan is so essential.
Proactive Fraud Detection Signals
Beyond just handling one-off failures, your system needs to be on the lookout for more coordinated, fraudulent attempts. This means digging into the metadata and behavioral patterns that often scream "bad actor." You’re not just verifying an age; you're assessing the trustworthiness of the entire interaction.
Keep an eye out for these classic red flags:
- VPN or Proxy Usage: Is the user actively trying to hide their real location?
- Disposable Email Addresses: Services that generate temporary emails are a common tool for creating throwaway accounts.
- Device Fingerprinting: Does this particular device have a known history of shady activity on other sites?
- Velocity Checks: Are you seeing a flurry of sign-up attempts from the same IP address in a suspiciously short time?
A truly robust system doesn't just react; it proactively sniffs out suspicious patterns. By combining these signals, you can automatically route high-risk users to more stringent verification steps before they ever get through the door.
Finally, for the highest-risk cases where you still have doubts, you can ethically request a selfie with a "liveness" check. This is where you ask the user to perform a simple action, like turning their head, to prove they're a real, live person right at that moment. This step must be handled with extreme care, requiring explicit consent and a clear explanation of why it’s necessary. This final layer helps you confidently verify age without ever needing an ID, all while maintaining a secure and fair environment for your genuine users.
Your Questions, Answered
Stepping away from old-school ID checks brings up a lot of questions. It's a smart move, but you want to get it right. From legal fuzzy areas to the user experience, I've seen platform owners run into the same challenges. Let's clear up some of the most common ones.
Is It Really Legal To Verify Age Without a Government ID?
Yes, it is. And honestly, it’s often the preferred approach.
Modern regulations, like the UK's much-discussed Online Safety Act, are pushing for a risk-based strategy. They don't demand one specific method. The law simply says you have to take reasonable steps to keep minors out. It never says those steps have to involve collecting sensitive government documents.
In fact, using alternatives like financial data checks, hooking into a third-party age assurance network, or implementing well-tuned facial age estimation is increasingly seen as the more privacy-conscious way to meet your legal duties. The goal is to have a system that actually works, not just one that collects the most data.
How Accurate Is Facial Age Estimation, Really?
It can be surprisingly accurate. Top-tier systems are hitting 95–99% accuracy when determining if someone is over or under a threshold like 18.
But—and this is a big but—accuracy isn't a single, simple number. Real-world conditions matter. Things like bad lighting, a fuzzy webcam, or even demographic blind spots in the AI's training data can throw things off.
That’s precisely why you should never rely on facial age estimation alone. Treat it as a fast, low-friction first pass. If the system flags someone as potentially underage, your flow should automatically and smoothly offer them another way to prove their age. This ensures you don't lock out legitimate adults by mistake.
What's the Difference Between Age Verification and Age Assurance?
This is a really important distinction, and it gets to the core of why these new methods are so much better.
Age Verification is the old-school way. It’s about proving an exact age or date of birth, usually by forcing a user to upload a driver's license or passport. It's about knowing someone is exactly 21 years and 3 months old.
Age Assurance is a much more elegant concept. It’s focused on simply confirming that a user meets an age threshold. Is this person over 18? Yes or no? That's all you need to know. This approach gives you that simple "yes/no" answer without you ever having to handle, store, or protect their actual birthday.
For nearly every platform, age assurance is the goal. It delivers strong protection with the absolute minimum amount of data collection, which is exactly what users want.
How Can Minors Be Verified Without an ID?
This comes up a lot for platforms with content for teens, but not for younger kids. The most common and accepted path is parental consent.
Regulations like the Children's Online Privacy Protection Act (COPPA) lay out a clear framework for this. Essentially, a parent or guardian vouches for their child.
The parent will go through an age check themselves, often using their credit card or another method only an adult would have. This creates a clear line of responsibility where the verified adult is granting access to the minor. It's a practical way to manage access for younger, but still age-gated, audiences.
At Luvr AI, creating a safe, private, and deeply immersive experience is everything. Our advanced AI companions are built for an adult audience, and our commitment to seamless, privacy-first age assurance is how we keep our community secure and trusted.
If you're ready for a new world of connection and storytelling, come see what we've built.